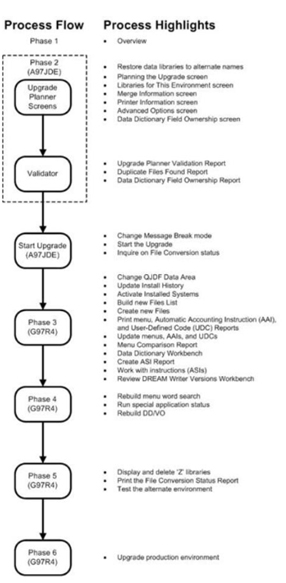
Upgradation JD Edward A7.3 to A9.2
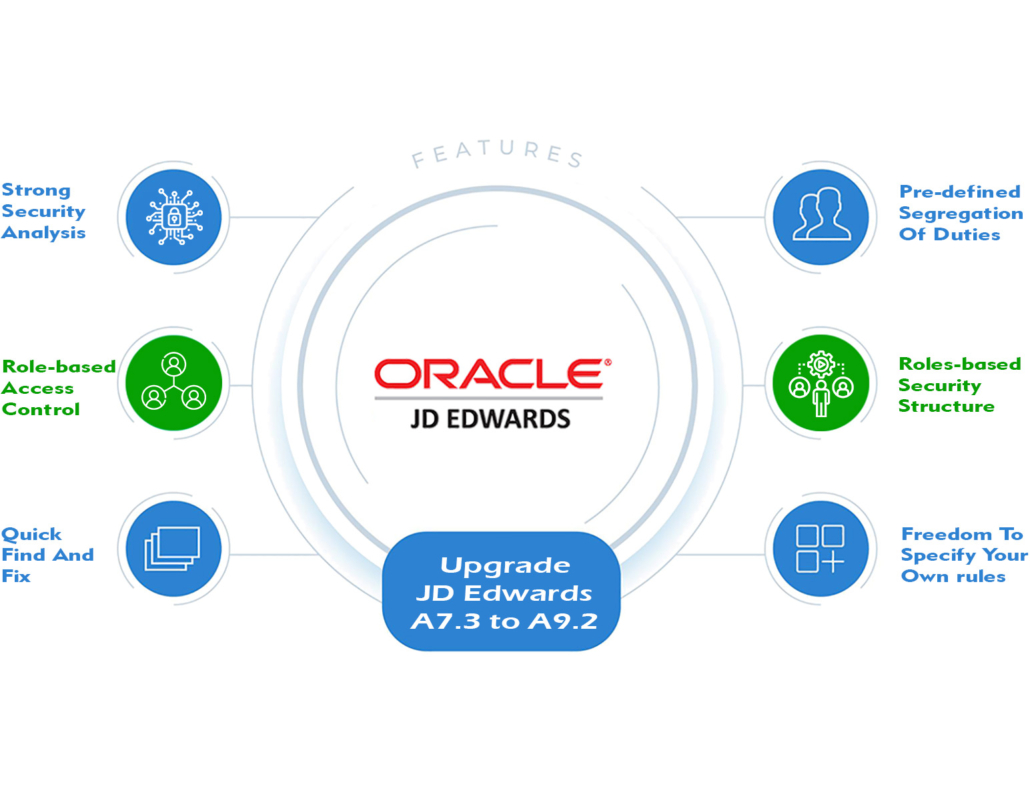
Never has JD Edwards World security been so quick and easy to implement and manage. With over 15 years’ experience of World security and our unique ability to facilitate multiple role-based access control, Q Software is uniquely able to offer you:
- The strongest security analysis, capable of distinctly identifying back-door entry points to important programs
- Quick “find and fix” – once you’ve found a security vulnerability, you can patch it right away.
- Pre-defined Segregation of Duties (SoD) – but you have the freedom to specify your own rules at either the program, function, or roles level. Pre-defined roles-based security structure – but you don’t have to use our roles, it’s quick and easy to define your own.
- Multiple roles, where a user’s security alters based on the roles, they are playing at any one time. He need not even log out.
- Particular SoD enforcement when you change a user’s role. Comprehensive reporting to meet all your auditor’s needs. Different severity levels can be set to either prevent violations or merely alert you that you will lead to one.
The Problem:
Security Administration Only a minimal amount of security is offered by World’s security facilities. Users frequently have to pick between job freedom and security. An All Doors Closed security strategy is nearly impossible to configure and monitor, and effective security management calls for a level of expertise that is lacking in many organizations.
The Solution:
World SoD offers tools to help you fine-tune your SoD model as well as a SoD model based on feedback from security officers and top audit firms. World SoD reports the controls you have in place to your auditor. You can even manage your SoD policy across various roles when paired with World Config.
The Problem:
Review & Reporting How to spot and address potential security and compliance issues PRIOR to them having an impact on your business, such as function key access, other back-door access, and insufficient action code security. How to create reports for your auditors that demonstrate compliance with regulations by outlining who has access to important programs, how they get there, and where else they can go using function keys or low-level commands
The Solution:
You can use the World Analyzer to examine important facets of your JD Edwards World security. Security can be immediately and successfully identified. You can feel secure knowing you have established an effective security platform you can rely on, making ongoing control manageable. Weeks of work are reduced to days by the World Analyzer.

 020-46036203, 46036206
020-46036203, 46036206 +971502180530
+971502180530 info@nwssoft.com, hr@nwssoft.com, jobs@nwssoft.com
info@nwssoft.com, hr@nwssoft.com, jobs@nwssoft.com  NWS Soft Consulting Pvt. Ltd.
NWS Soft Consulting Pvt. Ltd.
